CORE.SYS XBOX KEY/CODE
Content: text (16 symbols)
Available: 1
Uploaded: 02.09.2025
Positive responses: 0
Negative responses: 0
Sold: 0
Refunds: 0
Seller: GamingParadise
information about the seller and its items
Loyalty discount! If the total amount of your purchases from the seller more than:
| $10 | the discount is | 1% |
| $100 | the discount is | 2% |
| $400 | the discount is | 3% |
| $1000 | the discount is | 4% |
~ $8.79
The exact amount is on the payment page
🔥 After payment you will automatically receive:
🔑 Code: CORE.SYS. 🔥
🗝️You will receive the key in your personal account at www.oplata.info
📧A link to the product page and instructions will be sent to your email address provided at purchase.Supported Platforms:
✅Xbox One🎮💥
✅Xbox Series S|X🎮🔥 OPTIMIZED
✅ After activating the key, the product will be accessible from any region.
🌏For successful activation, your IP address must match the key´s region.🌏💡You will receive all the tools for successful activation, as well as very detailed instructions📚📱💻Pre-activation overview using phone or computer:
1️⃣. ⚠️Go to account.microsoft.com/profile and set the region indicated with the key.⚠️
2️⃣. ❗Your IP address must match the key´s region.
3️⃣. 🔗Go to redeem.microsoft.com and activate the key
4️⃣. 🤔If you encounter an activation error - carefully read the 🗒️️´USAGE INSTRUCTIONS´🗒️️on your order page
5️⃣. 📥Ready to download, enjoy your purchase.
🚨If after successful activation the desired product does not appear in your library, then you need to go to your console settings and change the region to the one indicated with the key. Then go to the store, find the product, and instead of ´buy´ button, you will have ´install´
💬We are confident you can handle this, but if any problems arise, we are always ready to help!🤗
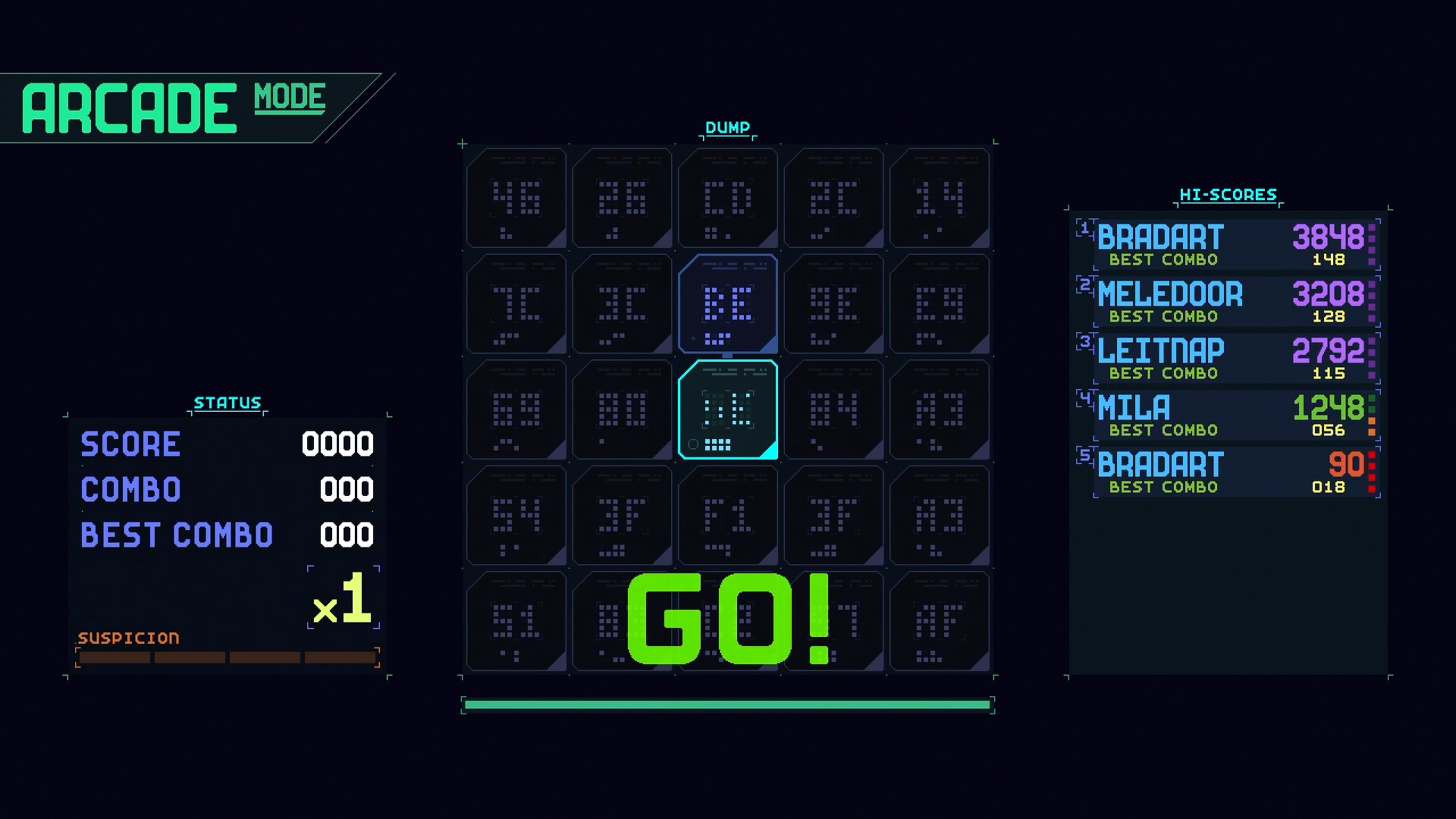
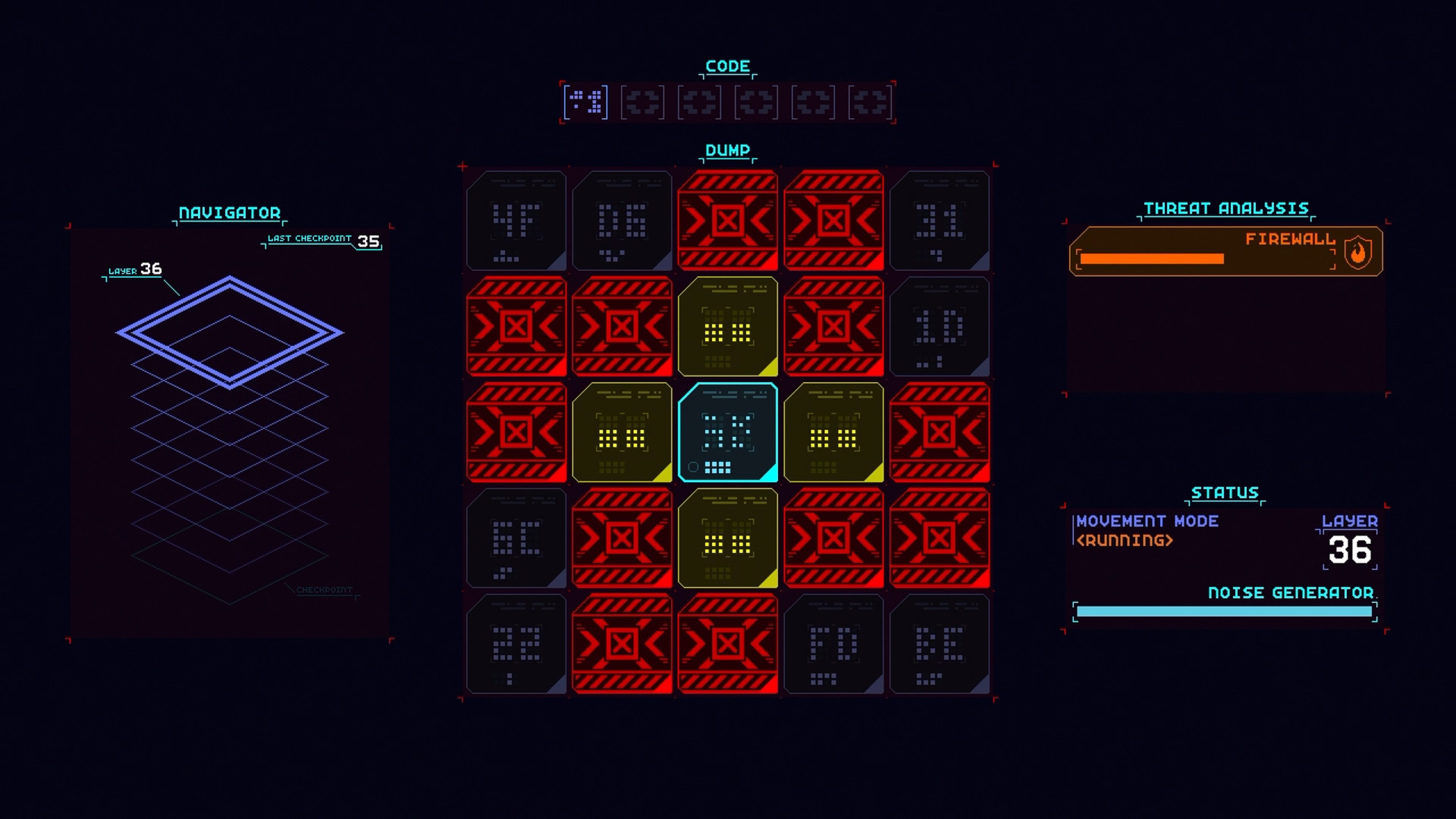
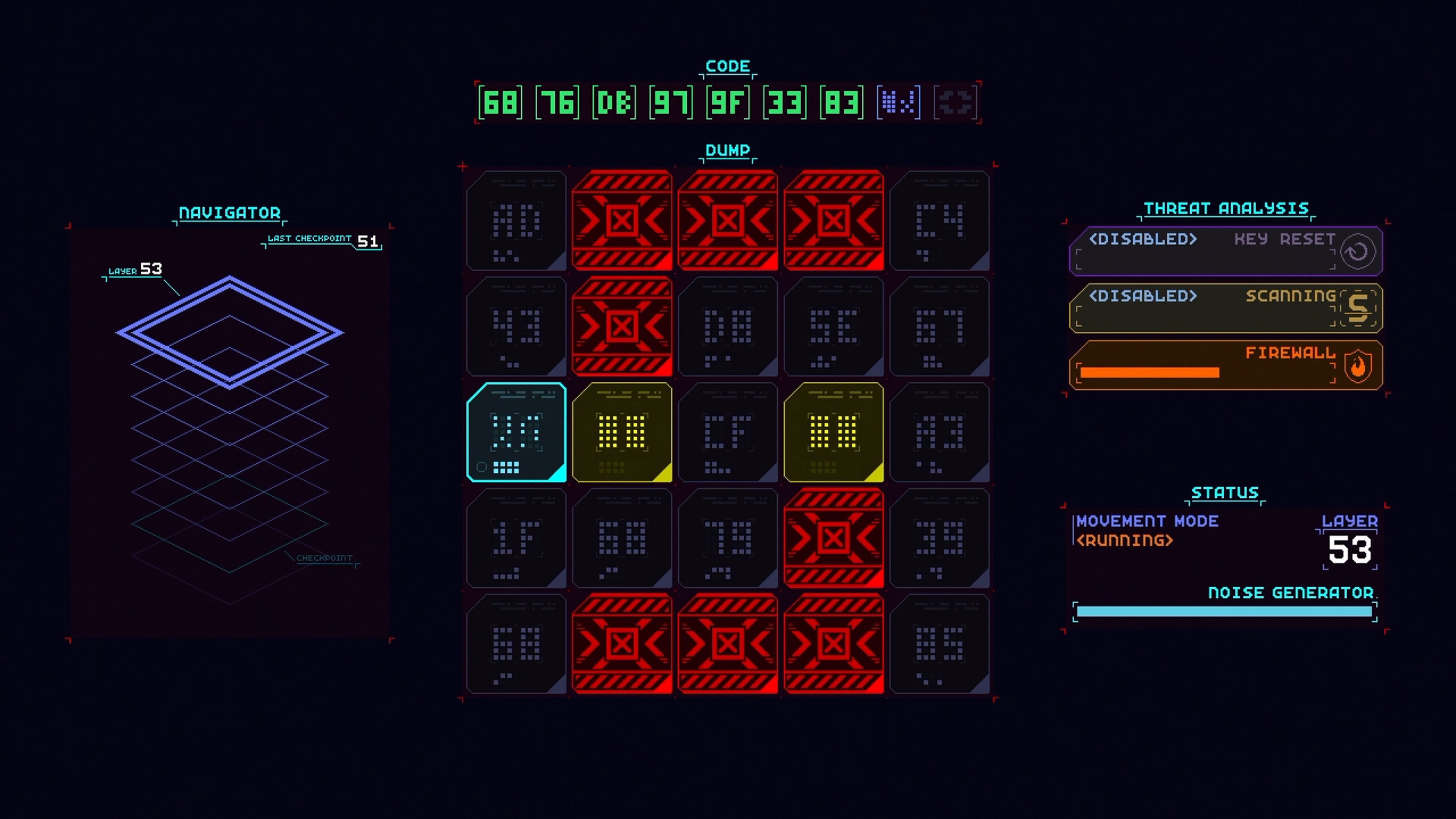
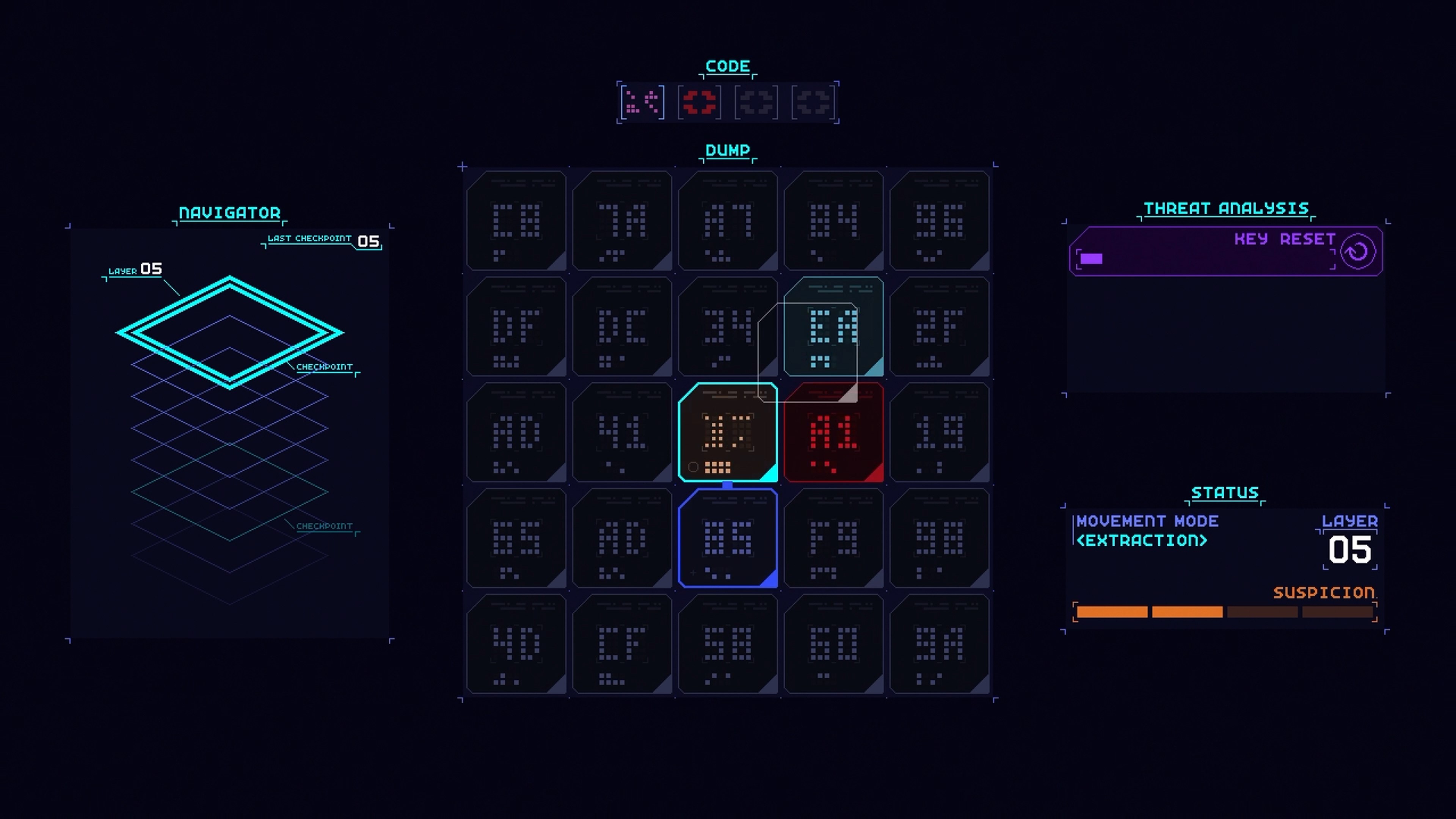
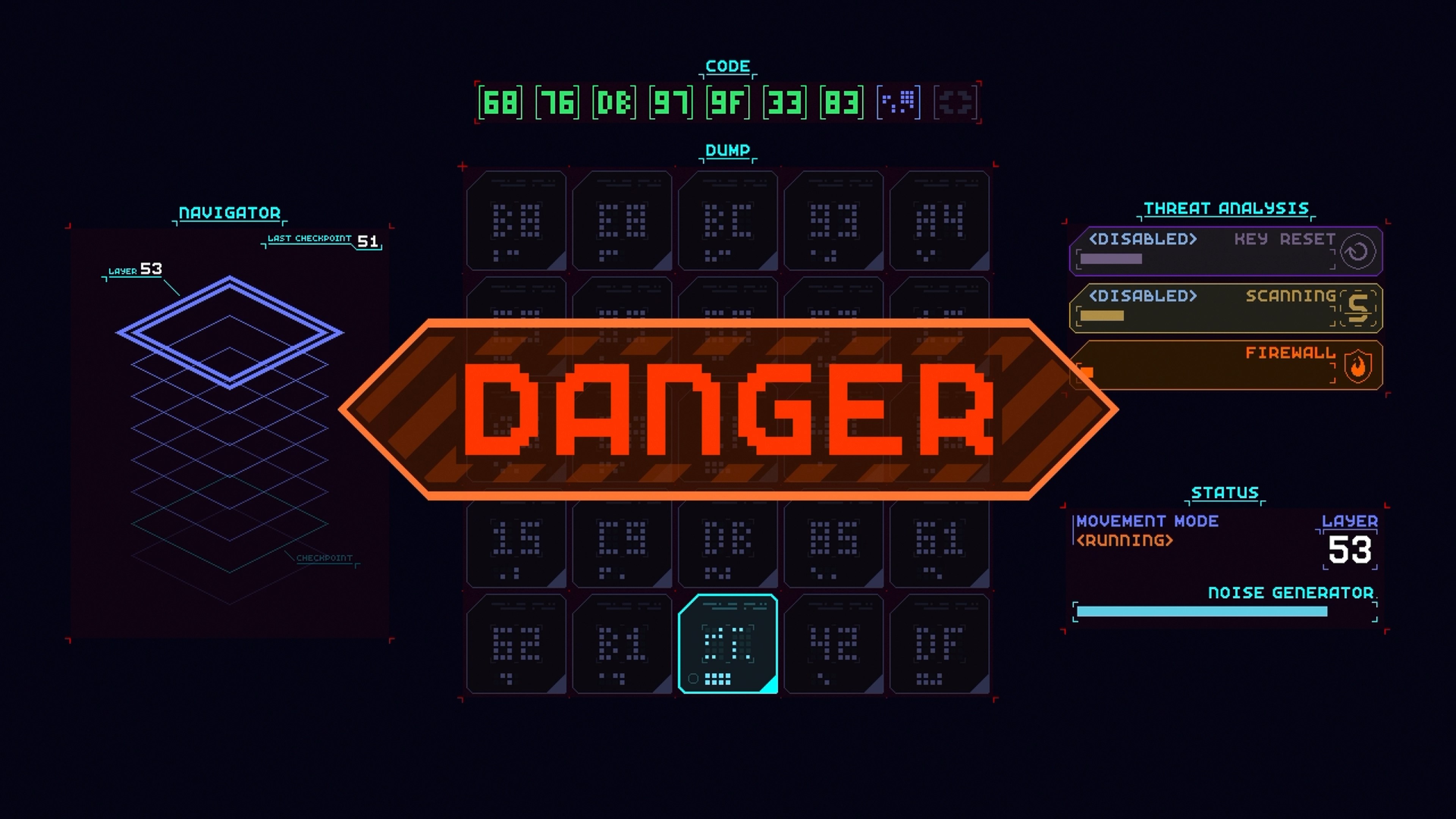
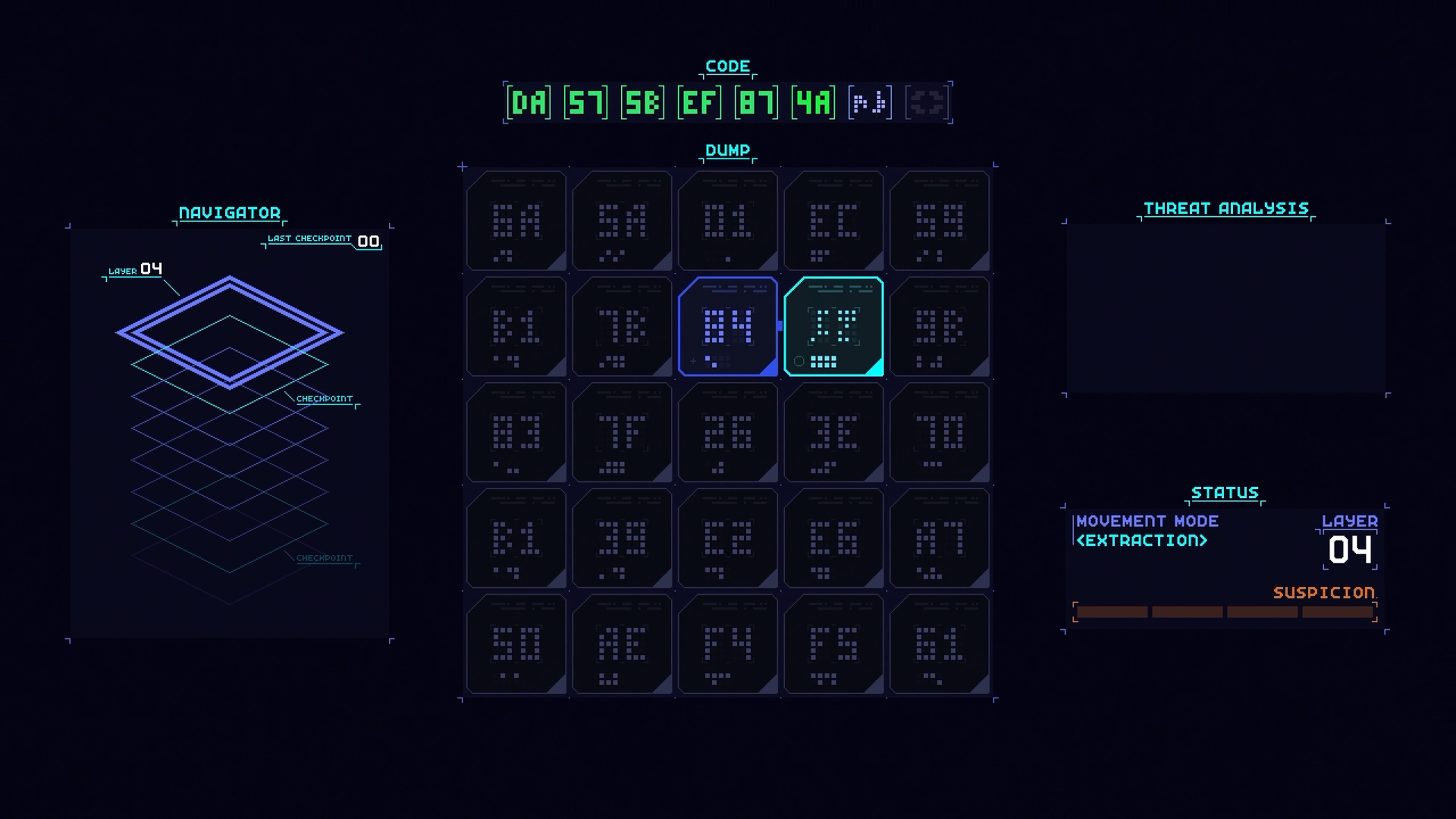
Get ready to hack your way through increasingly complex computer systems in retro arcade style! CORE.SYS is a brainteasing action puzzler where you’ll need to break through layers of digital security with quick-thinking strategy. Move your cursor around a 5x5 grid of alphanumeric key panels, use your scanning ability to identify the next piece of code needed and select that panel to complete the code sequence, thus bypassing security and gaining access to the next layer.
Be careful, though! The deeper you hack, you’ll have to contend with more intense firewall sweeps. Can you locate the data you need to extract and get out clean?
🔑 Code: CORE.SYS. 🔥
🗝️You will receive the key in your personal account at www.oplata.info
📧A link to the product page and instructions will be sent to your email address provided at purchase.Supported Platforms:
✅Xbox One🎮💥
✅Xbox Series S|X🎮🔥 OPTIMIZED
📦Type: Game
🗓️release date: 20.08.2025
| 💾Size: 387.0 МБ👨💻🛠️👩💻Developer: Eastasiasoft Limited, NipoBox
✅ This product remains within your Microsoft account!🗓️release date: 20.08.2025
| 💾Size: 387.0 МБ👨💻🛠️👩💻Developer: Eastasiasoft Limited, NipoBox
✅ After activating the key, the product will be accessible from any region.
🌏For successful activation, your IP address must match the key´s region.🌏💡You will receive all the tools for successful activation, as well as very detailed instructions📚📱💻Pre-activation overview using phone or computer:
1️⃣. ⚠️Go to account.microsoft.com/profile and set the region indicated with the key.⚠️
2️⃣. ❗Your IP address must match the key´s region.
3️⃣. 🔗Go to redeem.microsoft.com and activate the key
4️⃣. 🤔If you encounter an activation error - carefully read the 🗒️️´USAGE INSTRUCTIONS´🗒️️on your order page
5️⃣. 📥Ready to download, enjoy your purchase.
🚨If after successful activation the desired product does not appear in your library, then you need to go to your console settings and change the region to the one indicated with the key. Then go to the store, find the product, and instead of ´buy´ button, you will have ´install´
💬We are confident you can handle this, but if any problems arise, we are always ready to help!🤗
🤝Only here can you buy keys without intermediaries at a favorable price.
💰Discounts are included for all subsequent purchases💵
📜Detailed product description: Break in, retrieve highly protected data and get out clean in a fast-paced hacking simulation!💰Discounts are included for all subsequent purchases💵
Get ready to hack your way through increasingly complex computer systems in retro arcade style! CORE.SYS is a brainteasing action puzzler where you’ll need to break through layers of digital security with quick-thinking strategy. Move your cursor around a 5x5 grid of alphanumeric key panels, use your scanning ability to identify the next piece of code needed and select that panel to complete the code sequence, thus bypassing security and gaining access to the next layer.
Be careful, though! The deeper you hack, you’ll have to contend with more intense firewall sweeps. Can you locate the data you need to extract and get out clean?
🌟 Common activation errors and their solutions you may encounter:
❌ ´This code cannot be used...´ - Your IP address does not match the key´s region.
🔍 ´Unable to find this product. This code is already invalid´ - Change the account´s region to the key´s region.🧩If for any reason you cannot or do not want to activate the key on your account, we can do it for you! Simply use this service:
https://boardrussia.ru/digital-shop/item/3837565 you purchase this product by mistake - I cannot issue a refund, as you already know the code.📌
❌ ´This code cannot be used...´ - Your IP address does not match the key´s region.
🔍 ´Unable to find this product. This code is already invalid´ - Change the account´s region to the key´s region.🧩If for any reason you cannot or do not want to activate the key on your account, we can do it for you! Simply use this service:
https://boardrussia.ru/digital-shop/item/3837565 you purchase this product by mistake - I cannot issue a refund, as you already know the code.📌
No feedback yet